Security in IoT devices
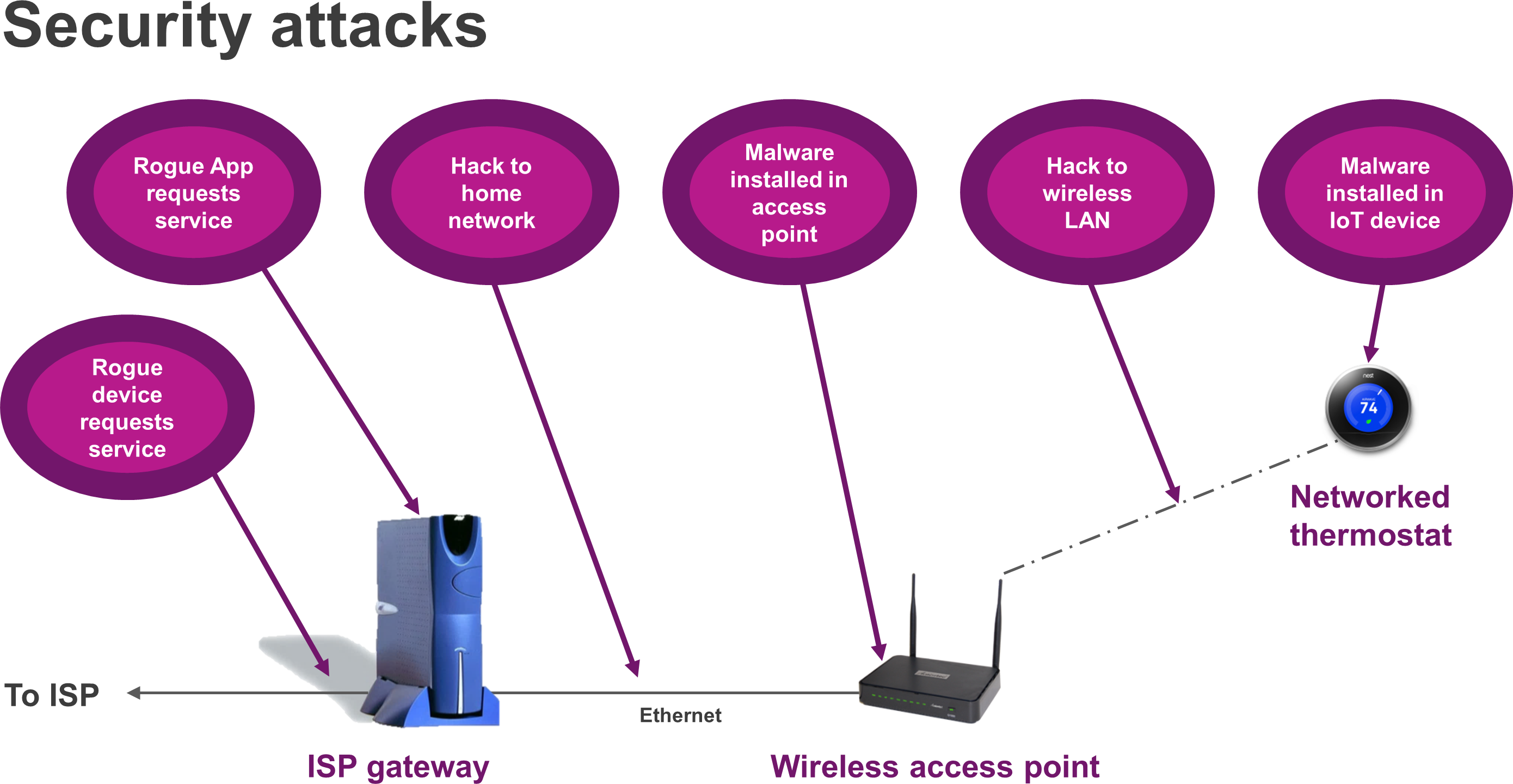
A key requirement for IoT applications is security. IoT opens up networks to a variety of threats as more and more devices are connected to a network and eventually to the cloud. The figure below shows an example of an IoT device for home automation connected to a home network with possible threats to the network security.
At the edge of the network, as multiple IoT devices are added, the potential threats are greatly increased. The threats to networks with connected devices are documented and are newsworthy. The LifX brand of connected LED bulbs have been reported as being able to leak wireless security information.
IoT devices must provide be capable of providing a robustly secure environment. Security in IoT is achieved in the following ways:
- Secure boot
- Secure code update
- Key protection
- Tamper resistance
- Access control of secure resources
- Secure DMA (direct memory access) with data encryption for critical functions
- Session authentication
Secure boot
When the IoT device is powered up and begins execution, the system must start execution with trusted code at boot time. In an IoT system, the trusted execution can be accomplished by having a secure CPU run trusted code on chip. This trusted code must have its credentials secured from the time the credentials leave the secured credentialed vault to the time the code is implemented on the IoT device. The secure boot code must not be capable of being tampered.
Imagination has developed and licenses IP that provides the secure boot feature required in IoT systems; find out more about our OmniShield security technology and the benefits it brings to a range of connected devices.
Secure code update
An IoT device can be hacked by corrupting the embedded software with malware. To protect against this type of attack requires the firmware to be properly credentialed and downloaded to the IoT device in a secure manner. The secure update (available as an IP block from Imagination) is accomplished by means of including the hardware required on the IoT device to be encapsulated within a cryptographic boundary.
The updated firmware is encrypted and downloaded to the IoT device where it decrypted and credentials are checked; this is an important use case in consumer devices where software updates are provided for bug fixes (including security improvements) as well as adding additional functional capabilities to the IoT device.
Key protection
Private keys consist of a set of addresses of OTP (one time programmable) memory which can be programmed with keys for encryption, authentication, and device identifier. The memory needs to be configured on chip such that:
- OTP is not accessible via external pins of the IoT SoC device
- OTP memory contents may be encrypted
- OTP memory contents are accessible only by ‘trusted processes’ running on the application processor
Tamper resistance
Simple Power Analysis (SPA), Differential Power Analysis (DPA) and High Order Differential Power Analysis are techniques whereby analysis of the power and other electrical emissions from a semiconductor device can provide information about the encryption techniques and codes used. These emitted signals are a point of attack that requires countermeasures. These attacks are addressed to the CPU and associated hardware that runs encryption and decryption. MIPS M-class CPUs are tamper resistant by implementing the following countermeasures including user-defined scrambling of cache memory address and data and injection of random pipeline stalls.
Access control of secure resources
In an IoT system where a device is sending proprietary data or is engaged in commerce, the software processes running on the device are required to have secure access to peripherals and memory. This is needed to maintain security and to ensure malware cannot access the same information in memory or on peripherals as may be required by the secure processes. Consider the following example where a medical device may measure certain data on an individual, where such data is controlled by the HIPAA laws in the United States.
Also this example assumes that a second process is running that is communicating with a medical insurance company to validate insurance. In this case there may be multiple processes running on the CPU, but there are two processes running that are required to be secure and isolated. In this type of situation virtualization is required in order to isolate the hardware resources committed to each of the secured processes running on the CPU, illustrated in the figure below.
It is worth pointing out that all MIPS CPUs support hardware virtualization, from the microcontroller range (M-class) to high-end application processors (P-class).
Secure DMA
DMA transfers to memory in a secure IoT device must be encrypted. The DMA engine and associated peripherals and memory should be encapsulated with in an encryption boundary such that any transfers into or out of the memory boundary will be encrypted or decrypted respectively.
OmniShield White Papers
If you are interested the latest IoT-related news and updates from Imagination, make sure to follow us on Twitter (@ImaginationTech, @MIPSguru, @MIPSdev), LinkedIn, Facebook and Google+.