Why MIPS is needed to secure tomorrow’s connected devices
Every day seems to bring a new, connected device to the market promising to improve our lives. It might be a doorbell, a car, or a drone, but whatever it is, to make it relevant in today’s world it must be connected and as a consequence, ‘smart’.
However, the flipside of this accessibility is vulnerability, as providing access for a known party, by definition, means it could also be accessed by those who would wish to do harm.
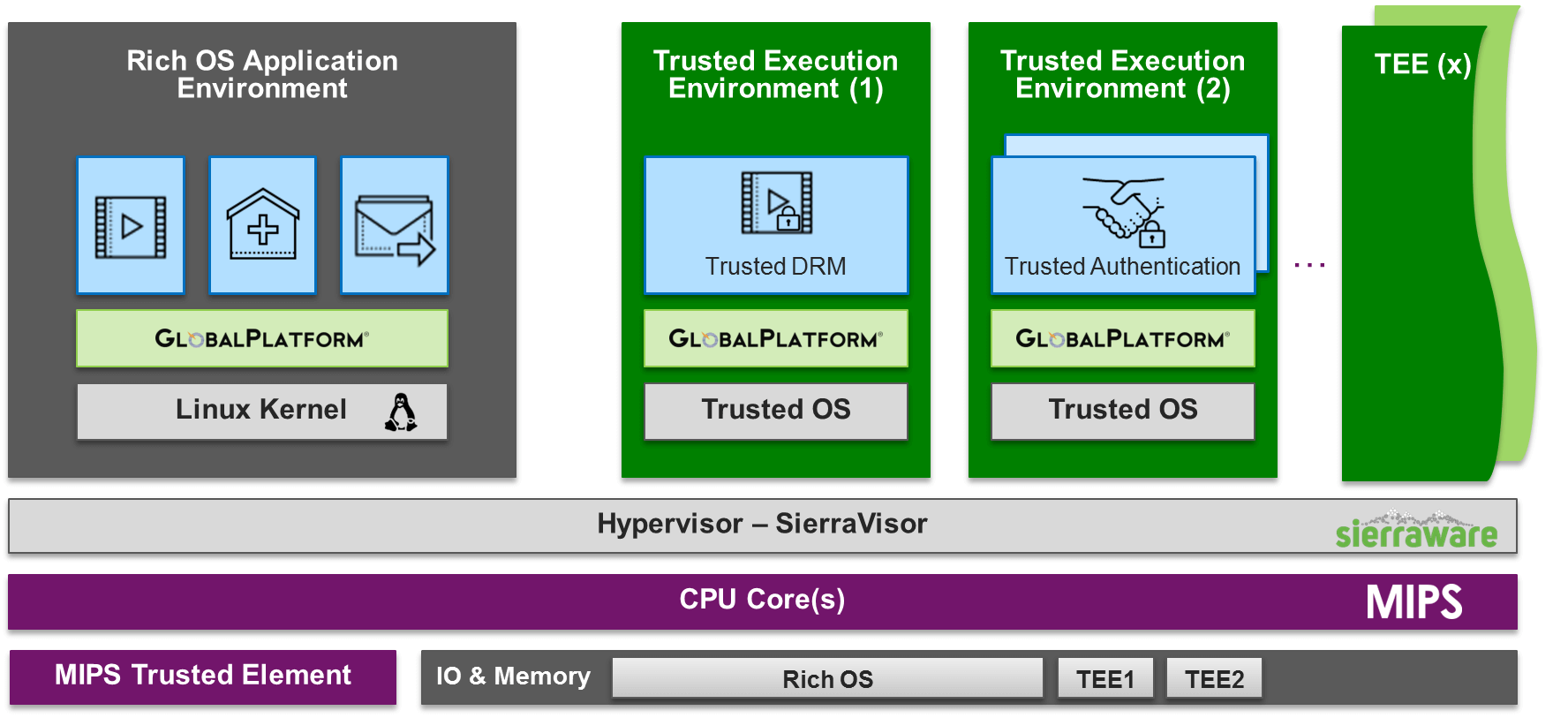
We can all agree then that security for these devices is a must. This is where the idea for a Trusted Execution Environment (TEE) stems from. A TEE sits at the heart of connected embedded devices and provides a secure area within which sensitive data is stored, processed and protected. The TEE ensures that this is an isolated, trusted environment — enabling end-to-end security by offering isolated, safe execution of authorized software. In other words, the TEE represents a region of an SoC that is separate, allowing for the execution of trusted applications (TAs) in a safe, secure silo.
However, programming applications to make use of this can be challenging, and without a common method of doing so, applications will need to be custom developed for different hardware, which adds complexity and extends time to market. To combat this, a consortium of companies have come together to form GlobalPlatform, creating application programming interfaces (APIs) for TEEs. This makes it easier for developers to make use of the TEE, enabling interoperability, enhancing ease of adoption and reducing the time to market.
For this to be possible, it’s important then that TEEs are created that fully conform to the GlobalPlatform standard.
In addition, however, we believe that what is needed is a ‘multi-trust’ TEE – that is where trusted applications are not just placed together in a single secure environment, but are isolated from each other in individual, protected silos. This means that if an attacker does compromise one application the others are not compromised at the same time.
This is of critical importance in cases such as a set top box, where multiple end-user applications could reside from different vendors, each with sensitive data to protect, such as payment details or a DRM protected video stream.
We call this ‘security by separation’.
Hardware virtualization, as offered by technology as found in MIPS CPU cores making it possible to create these secure ‘domains’ in which trusted applications can securely reside. Our blog post here goes into more detail on the business benefits of this and how it would be implemented in a home gateway.
On Tuesday 12 September, MIPS will be participating in the 5th annual Trusted Execution Environment (TEE) Seminar, presented by GlobalPlatform, at the Sheraton Grand Dongcheng Hotel in Beijing.
Here, we will demonstrate our GlobalPlatform Compliant TEE for MIPS solution. Created in combination with Sierraware, a pioneer in virtualization and security, the SierraTEE is built on MIPS’ CPUs and is fully GlobalPlatform compliant.
At the event, Volker Politz, the vice president of segment marketing at MIPS will moderate a panel discussion and Q&A session on DRM, and its importance of creating compliant hardware for mobile devices, tablets, set-top boxes and smart TV.
If you’re in the Beijing area and want to understand the challenges in protected connected devices and see working solutions first-hand, you’ll want to be at this event.
To learn more about it go to this page. You can follow the link at the bottom of the to register.
We have limited free tickets available so if you’d like to attend please get in touch at: marcomms@mips.com
Also, to stay up-to-date with news from MIPS you can follow us on social media on Twitter @mipsguru and on LinkedIn, Facebook.